Apple works hard to make its software secure. Beyond primary protections that prevent malware infections in the first place, company engineers also build a variety of defense-in-depth measures that are designed to lessen the damage that can happen once a Mac is compromised. Now, Patrick Wardle, a former National Security Agency hacker and macOS security expert has exposed a major shortcoming that generically affects many of these secondary defenses.
In a presentation at the Def Con hacker convention in Las Vegas over the weekend, Wardle said it was trivial for a local attacker or malware to bypass many security mechanisms by targeting them at the user interface level. When these security measures detect a potentially malicious action, they will block that action and then display an alert or warning. By abusing various programming interfaces built into macOS, malicious code could generate a programmatic click to interact or even dismiss such alerts. This "synthetic click," as Wardle called it, works almost immediately and can be done in a way that is invisible to the user.
“The ability to synthetically interact with a myriad of security prompts allows you to perform a lot of malicious actions,” Wardle told Ars. “Many of Apple's privacy and security-in-depth protections can be trivially bypassed.”
With the ability to generate synthetic clicks, an attack, for example, could dismiss many of Apple's privacy-related security prompts. On recent versions of macOS, Apple has added a confirmation window that requires users to click an OK button before an installed app can access geolocation, contacts, or calendar information stored on the Mac. Apple engineers added the requirement to act as a secondary safeguard. Even if a machine was infected by malware, the thinking went, the malicious app wouldn’t be able to copy this sensitive data without the owner’s explicit permission.
Though many of Apple's security alerts attempt to detect and ignore synthetic clicks, Wardle discovered that the privacy alerts, even on a fully updated High Sierra system, were not protected. "What is the point of displaying an alert, if malware can simply dismiss it?" he asked.
In the past, malware has abused such synthetic clicks to perform a variety of nefarious actions. For example, the sneaky Genio adware, DevilRobber currency mining malware, and the insidious Fruitfly malware that stole millions of images from infected Macs over a 13-year period all used synthetic clicks to bypass defense-in-depth warnings.
Apple responded to these in-the-wild wares by improving the security of its operating system. Now, in recent versions of macOS, security alerts and prompts will ignore synthetic events. At least that was the idea. In his presentation, Wardle first illustrated how an attacker could abuse a feature of macOS called "mouse keys" that would convert keyboard keypresses into mouse movements. Mouse keys lets a user move a mouse up, down, to the right or left, or in diagonal directions by pressing certain keys as diagrammed below:
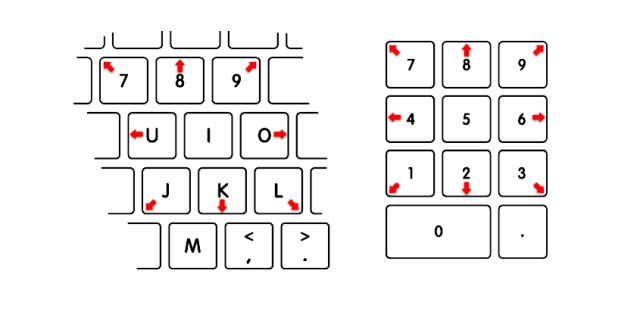
However, Wardle illustrated how an attacker or malware could also leverage "mouse key" events to generate synthetic mouse clicks that would be accepted, even by "protected" security alerts. After creating a proof-of-concept attack that could interact and dismiss the keychain's access prompt and dump a user's unencrypted passwords and private keys, he reported the issue to Apple, which released a supplemental update to patch it as CVE-2017-7150. Now "mouse keys" are ignored by security alerts, and keychain access always requires a user's password.
But even after Apple issued the patch, the warnings could still be bypassed. While testing an older attack, Wardle incorrectly copied and pasted some code. Without realizing the mistake, he ran the code, which to his amazement allowed him to post synthetic clicks to security alerts, even on a fully patched High Sierra system. Digging deeper, he realized that his buggy code was sending two mouse "down" events (instead of the typical mouse down, mouse up event).
"The system converts the second mouse down event to a mouse up event" he noted. "But since this mouse up event is generated by the system, it is allowed to interact with security prompts." As a result of this issue, Wardle was able to completely bypass the warnings when doing a variety of things that have serious security and privacy consequences. The most worrisome is bypassing a newly introduced Apple security mechanism designed to prevent the programmatic loading of “kexts,” which are kernel extensions that interact with the core of the macOS.
Apple representatives didn't respond to an email seeking comment for this post. Wardle, for his part, said the bypass raises questions about how the company rolled out the improvements. “I wasn’t trying to find a bypass, but I uncovered a way to fully break a foundational security mechanism,” said Wardle, who is the developer of the Objective-See Mac tools and chief research officer at Digita Security. “If a security mechanism falls over so easily, did they not test this? I’m almost embarrassed to talk about it.”
This post was rewritten for clarity and grammar fixes.
reader comments
73